
China has recently accused the United States of sending a network attack on China, but this time the allegations are more targeted and tougher. A Sino -US offense and defense in the field of network security have begun.
On September 6, the National Computer Virus Emergency Treatment Center (CVERC) accused the National Security Agency (NSA) "Specific Invasion Action Office" (TAO) in Northwest Industry in Northwest Industry, located in Xi'an, Shaanxi ProvinceThe university launched a network attack and stole core technologies such as key network equipment configuration, network management data, and operation and maintenance data.
Then, the Chinese official media has disclosed more information on the above cases twice.First of all, last Thursday (September 22) refers to the control of the China Telecom Network in the process of TAO's launching network attack; this Tuesday (September 28) then pointed out that the department has inquired about a group of sensitive identity in China in China.Essence
It is common to mobilize or bear network attacks between countries around the world, especially between large countries.However, China ’s accusations have attracted attention today, because Chinese officials have changed their long -term“ defensive ”on cybersecurity issues, but instead defended the attack, and pointed the spearhead to the US department more high -profile and clearly.
Northwestern University of Technology was locked
Northwestern University of Technology discovered the traces of the Trojan -horse program network attack in the school information system in April this year, and issued a statement alarm in June.After analyzing the joint technology team composed of CVERC and China Network Security Enterprise 360, the report issued by CVERC preliminary judgment of the attack source of the attack is the TAO of the NSA. It also points to Robert Edward Joyce, who is the director of NSA network security.It is behind the scenes of the invasion.
CVERC reports that Tao has implemented tens of thousands of network attacks on China's domestic network targets in recent years, controlled network devices such as network server, router, and stole more than 140GB of "high -value data".
Chinese Ministry of Foreign Affairs spokesman Mao Ning said at a regular press conference on September 5 that the report "exposed another example of the US government's network attack on China."She also criticized the United States for a long time to "conduct no differential voice monitoring of Chinese mobile phone users, illegally steal the text message content of mobile phone users, and make wireless positioning."

Public information shows that Northwestern University of Technology is directly affiliated to the Ministry of Industry and Information Technology of China, and is known as one of the "National Defense Schools" in China.The Chinese government and the military have close relations.The U.S. Department of Commerce included the school in the "entity list" on the grounds of national security in 2001 to limit its acquisition of US technology.
Jin Qi, deputy director of the Beilin Branch of the Xi'an Public Security Bureau of Shaanxi Province, who accepts the case, told CCTV News that because of the special status of Northwestern University of Technology, and a university engaged in sensitive scientific research, it became a target of this online attack.Sexual goals.
Bloomberg reported on September 6 that the US NSA and the US State Department refused to criticize China.
Strategic considerations issued by China report
The United States NSA is not the first time that it has been named for online attack.In a report released by China Network Security Company Qi'an Pan Ancient Lab in February this year, it refers to the "Formula Organization" of the NSA hacker organization "Formula" to China, Russia, Japan and other 45 countries and regions for more than ten years.In March of this year, CVERC also reported that NSA deployed a remote Trojan called "NOPEN" to remotely control Internet devices around the world and steal user privacy data.
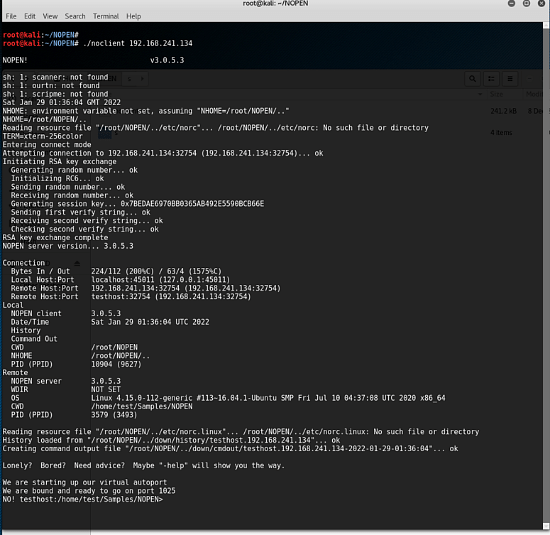
From the previous emphasis on the victims of the Internet attack, to the recent names to accuse the United States NSA.According to Chinese reports of BBC, this change marks that China is changing the network strategy. Just as the United States, the United Kingdom, and the European Union have publicly accused China of hackers many times in the past, China has also begun to expose the American hacking behavior.
Adam Meyers, senior vice president of Crowdstrike, who is responsible for threatening intelligence, believes that Beijing may have political considerations behind this report.
Meyer analyzed from the Washington Post that this report was a cooperation with the Chinese cyber security company and the Chinese government.For 360 companies, this survey report can be used as a publicity to attract the market to pay attention to their intelligence products and capabilities; for the Chinese government, Beijing can use this to fight back China to steal American intellectual property rights.Or, China tried to release a message to the United States borrowing this report: "You have been putting pressure on us, and now we have to start pressureing you."
Rospino, who has worked in TAO (JOSH LOSPINOSO) believes that China wants to weaken the image of American intelligence units in the eyes of Asia -Pacific members in Japan, South Korea, Taiwan and other Asia -Pacific members.
According to Greg Austin, an expert at the China Institute of International Strategy, analyzed from Bloomberg, China is more directly targeted at the United States to regain diplomatic initiative from the United States and its allies worldwideAt the same time, the Chinese people have the awareness of American hacking activities.
The China -US political game of the network space
China has accused the United States of conducting network attacks with strategic purposes. Why not the United States?
Taking the "Advanced Persistent THREAT 10" in 2018 (APT10) hacker group as an example, two Chinese Zhu Hua and Zhang Shilong were accused of China ’s national security by the US Department of Justice at the time.The Ministry ordered to act and illegally stole intellectual property and commercial secrets of more than 10 countries including the United States, Europe, and Asia.
When the case broke out, China and the United States were negotiating.Douglas Paal, deputy dean of the Carnegie International Peace Foundation and director of the Asian project, believes that the United States wants to show this case to show the determination of Huafu to crack down on hackers.Obtain more chips in negotiations to protect American intellectual property rights.
It can be seen that in the network space, China and the United States have their own abacus, which also makes this unlimited and unlimited space a new battlefield for geopolitics between China and the United States.
Pakistani Communication researcher Ruqiya Anwar analyzed on the 13th of this month in Nanhua Early Newspapers, in this new type of network landIn fate politics, the intersection of politics and network space has gradually transitioned to the "low -level politics" (Low Politics ", which is concerned about economic, social, and cultural issues to the" High Politics "involving national survival issues.
Professor Zheng Yongnian, a professor at the Chinese University of Hong Kong (Shenzhen), believes that it is not easy for China and the United States to cooperate in such space, because big data has become a tool for information competition between the country.Great weakening has caused difficulties in cooperation between sovereign countries.

He wrote last August that in terms of the current China -US interaction, the final network space order will not be a diverse Internet, it is likely that there will be only three possibilities: 1. China, China in ChinaThe US network is completely "decoupled" and becomes a non -connected or internal network; second, incomplete decoupling, but deterrent each other; third, China and the United States have expanded two "regional networks" with each other.
Zheng Yongnian believes that if you develop in these three directions, the world will inevitably face an absolute unsafe state, because if a large country pursues absolute security, it will inevitably create an absolute insecurity for another big country.And another big country will inevitably counterattack, creating absolute insecurity for the "victim".
People often worry that the competition between China and the United States may detonate the popular war such as nuclear war and cause huge harm to the world.However, in the era of digitalization and network control of all large public infrastructure, if the online offensive and defensive warfare warfare has evolved into a hot battle, the damage it brings will not be lower than that of traditional wars.
Although everyone knows that the best -eyed people know that the optimal solution of this offensive and defensive war is the common criterion for cooperating to explore international network behavior, but like the topic of global warming and other universal values, network security issuesIt is more likely to be used as a bargaining chip, and it is difficult for big powers to reach consensus.
Before putting down the confrontation attitude in the big country, the game of the network space will only be further long -term and become a new friction point.And we can only expect that this crumbling Damocaris's sword will not fall so quickly.




